SAN FRANCISCO (PRWEB)
May 29, 2020
Amid widespread predictions that COVID-19 will generate a wave of financial and identity crime, Breach Clarity today released analysis of recent data breaches that identifies risk for COVID-19 scams. The San Francisco fraud prevention and detection technology firm used its proprietary algorithm to analyze more than 1,000 elements of these five data breaches to produce their respective risk ratings.
“Any crisis is a green light to cybercriminals and scammers,” said Jim Van Dyke, Breach Clarity CEO. “COVID-19 has created an enormous amount of uncertainty and chaos at a scale we’ve not seen before. People are scared, anxious and desperate for anything that might help them through this troubling time. That makes them incredibly vulnerable. And, if you consider their private information is floating around the dark web, just waiting to be purchased by an opportunistic scammer, it’s the perfect storm.”
COVID-19 scams take many shapes. The IRS, for instance, has urged Americans to watch for phishing scams by being extra careful with emails, texts and calls that mention “stimulus check.” The FTC issued a warning to consumers not to fall for offers of vaccinations and home test kits.
According to Van Dyke, not every data breach opens victims up to COVID-19 related scams, or at least not to the same degree. That’s because every data breach exposes a different types of information. Whereas the April 2020 breach of video conferencing app Zoom exposed email addresses, passwords and personal meeting URLs, for instance, the March 2020 breach of Tupperware.com exposed credit and debit card information and billing addresses.
Cybercriminals use each type of stolen data in unique ways. Email phishing scams, for instance, rely on a good, clean set of legitimate email addresses. Payment fraud, on the other hand, depends on accurate and complete credit or debit card data. COVID-19 scammers are relying heavily on socially engineering to make attacks on financial accounts. Contact information, account information and the identifiers consumers use to access those accounts, therefore, are of high value to COVID-19 scammers.
Breach Clarity’s analysis revealed that five recently reported data breaches put victimized consumers at greater risk of targeted scams. Those five are…
- Toondoo.com, reported January 2020, exposed emails, login credentials and device information, e.g. IP addresses
- LimeLeads, reported January 2020, exposed employer name and contact info, as well as work email addresses
- Health Share of Oregon, reported February 2020, exposed protected health information, healthcare insurance account numbers, Social Security numbers and more personal data.
- Tetrad, reported February 2020, exposed names and associated home addresses
- Marriott International, reported March 2020, exposed employer names, home addresses, emails and phone numbers
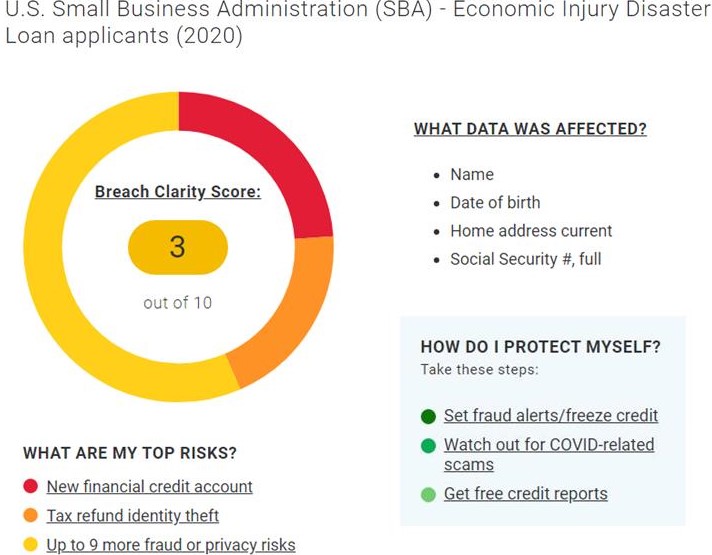
“While they didn’t break into the top five, a number of smaller breaches directly tied to COVID-19 assistance programs pose particularly concentrated risk to victims,” added Van Dyke. Those breaches include the U.S. Small Business Administration, which exposed data on nearly 8,000 small business owners applying for the Economic Injury Disaster Loan program, and the Arkansas Division of Workforce Services, which exposed the Social Security and bank account numbers of approximately 30,000 applicants for Pandemic Unemployment Assistance.
To explain how the firm determined which breaches presented greater COVID-19 scam risks, Breach Clarity COO Al Pascual said, “Essentially, the algorithm simulates the cybercriminal mindset. It considers the newly available, formerly private, data and calculates the attacks, tricks and traps that are most likely to be deployed with that intelligence.”
Consumers, reporters, analysts and others can access a Breach Clarity Score and threat analysis for the five breaches posing the greatest COVID-19 risk – or for any publicly-reported data breach – at BreachClarity.com. In addition to the score, the search results include the data types exposed in the breach, the specific risks the breach presents and a list of protective action steps victims can take to protect themselves. Search results for the U.S. Small Business Administration breach, for instance, look like the one above.
Share article on social media or email: